Stay Safe Online: Top 4 Tips from our IT Specialist
At Safe Ag Systems our team understand that our clients with agricultural businesses place their trust in our systems, and we make it our highest priority to ensure the security and confidentiality of their information. We are committed to protecting personal data and we implement the appropriate technical and organizational security measures.
Our cloud-based health and safety management system utilizes data encryption methods, and industry-standard security software and methodologies. Your data is also protected with your unique authentication credentials as well as access control ensuring the protection of your records.
Jump straight to our cyber security tips for agriculture.
What is cybersecurity?
We will start at the begin, think about the technology you are utilizing in your business, how are you reading this article. Is it in an email, from your desktop or on your phone? The aim of cybersecurity is to protect your personal information and your assets from attackers. These attackers can cause disruption to businesses as they target confidential information, impacting the integrity and availability of the information. Often attackers have one main goal to make money, they try to steal, change, or interfere with your information, affecting how a business operates.
.jpg?width=1920&name=Cyber%20security%20blog%20(2).jpg)
Common types of cyber-attacks:
Malware: Malware is a term for malicious software including viruses, spyware, trojans and worms. Malware gains access to essential information such as bank or credit card numbers and passwords.
Protecting against malware:
- Automatically update your operating system
- Automatically update your software applications
- Regularly back up your business’ data
Phishing: Pronounced ‘fishing,’ they are emails from individuals or organizations you ‘think’ you know. They mimic phrasing, branding and logos to appear ‘real,’ before conning users to click on a link or attachment.
Be cautious of:
- Requests for money, especially if urgent or overdue
- Bank account changes
- Attachments
- Requests to check or confirm login details
Ransomware
Ransomware attacks are typically carried out via a malicious but legitimate looking email link or attachment. When downloaded or opened, most ransomware encrypts a user’s files, then demands a ransom to restore access.
Secure your business when it comes to ransomware:
-
Update operating systems
-
Update software
-
Backup your business
How can you defend your business?
According to Beef Central, “Over 90 percent of successful attacks started with people error, and often involved simple “password laziness” such as employees using the same password and username across the board.”
At Safe Ag Systems, our team are committed to protecting your data and we have systems and processes in place to manage data security. We understand this topic can seem overwhelming, but it is a joint effort to keep your business information protected. Cybersecurity means cooperation between us and your team keeping their details safe.
.jpg?width=1920&name=cyber%20security%20blog%20(3).jpg)
Tips to keep safe when online
Securely organizing your software can drastically increase your business’ protection from the most common types of cyber threats. For example, your operating system is the most important piece of software on your computer. It manages your computer’s hardware and all its programs, and therefore needs to be updated, backed up and maintained. Improve resilience, stay up to date and stay safe with these software considerations for small businesses.
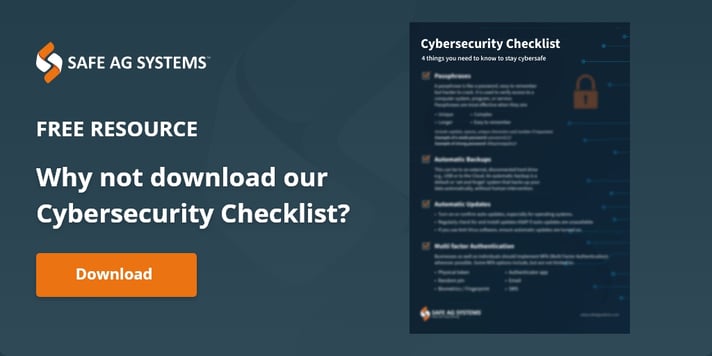
Passphrases
A passphrase is like a password. It is used to verify access to a computer system, program, or service. Passphrases are most effective when they are:
- Unique – not a famous phrase or lyric, and not re-used
- Longer – phrases are longer than words
- Complex – naturally occurring in a sentence with uppercase, symbols and punctuation
- Easy to remember– saves you being locked out.
Example for a weak password: A&d8J+1!
It is complex, hard to remember but only takes 2.5 hours to crack it.
Example for a strong password: I don’t like pineapple on my pizza!
It is easy to remember, complex and long. Takes more than 1 year to crack it.
Do not use names, birthdays on any personal information as a password.
It is recommended to change passwords regularly.
If you have trouble remembering them, use a password manager like LastPass or 1password.
Automatic Updates
An update is a new, improved, or safer version of a software (program, app or operating system like Microsoft Windows or Apple iOS) your business has installed on its computers or mobile devices. An automatic update is a default or ‘set and forget’ system that updates your software as soon as one is available.
- Turn on or confirm auto-updates, especially for operating systems
- Regularly check for and install updates ASAP if auto-updates are unavailable, especially for software
- Install updates as soon as possible (if auto-updates unavailable)
- Set a convenient time for auto-updates to avoid disruptions to business as usual
- If you use Anti-Virus software, ensure automatic updates are turned on
Automatic Backups
A backup is a digital copy of your business’ most valuable information e.g., customer details, sales figures. This can be to an external, disconnected hard drive e.g., USB or to the Cloud. An automatic backup is a default or ‘set and forget’ system that backs up your data automatically, without human intervention. Safely disconnecting and removing your back up storage device after each backup will ensure it is also not impacted during a cyber incident.
Multi factor Authentication
Multi-factor authentication typically requires a combination of something the user knows (pin, secret question), something you have (card, token) or something you are (fingerprint or other biometric).
Businesses as well as individuals should implement MFA (Multi Factor Authentication) wherever possible. Some MFA options include, but are not limited to:
- Physical token
- Random pin
- Biometrics / fingerprint
- Authenticator app
- SMS
MFA offers significantly more powerful security and protection against criminals.
They might manage to steal one proof of identity such as your PIN, but they still need to obtain and use the other proofs of identity to access your account.
With this cooperative effort, it means that our measures are implemented and monitored. This involves protecting your computers, phones, ensuring you have signed in and out, do not share your login details, you are responsible for managing your own account and never step away from your computer with sensitive information accessible.
If you are after more information check out the Small Business Cyber Security Guide.
Topics: Safety Management System
Disclaimer: Content on this website may be of relevance to users outside of Australia, but content links and examples are specific to Australia. Please check with your local authority for your country and industry requirements.